Eufy home security cameras have been storing your images unencrypted, researcher discovers
The company says it’s for thumbnail notifications
➡️ The Shortcut Skinny: your head (or face) in the clouds
🔐 Security researcher Paul Moore found images stored and easily accessible on Eufy servers
🤦 The data include face recognition thumbnails and personal identifiers, including usernames
🎞️ It’s possible to access RTSP streams with apps like VLC without authentication when on the same network and RTSP is enabled for the camera
🤔 Eufy app and marketing copy states that videos are never stored on servers, but does not address images
👍 Eufy has already taken steps to secure the images and promises to update its communication going forward
Update: When this story broke, I asked Eufy when we can expect updated language on its website and in its app communicating that snapshots and thumbnails will be temporarily stored in the cloud. I received a response, but it contained no information about when we should expect the changes. I’ve pressed further, but in light of the sensitive nature of the topic, it’s likely Eufy is being careful about any communication about this, for now. Here’s a snippet of Eufy’s statement:
We frequently review and test our security features and encourage feedback from the broader security industry to ensure we address all credible security vulnerabilities. If a credible vulnerability is identified, we take the necessary actions to correct it. In addition, we comply with all appropriate regulatory bodies in the markets where our products are sold.
It’s true that Eufy provides a means to report software security issues, and it even outlines its process for investigating and resolving vulnerabilities. In short, the company promises a turnaround time from reported issue to fix on a tiered system. Fixes for critical issues, it says, will be fixed within three days, high and medium risk vulnerabilities within 30, and low risk problems they promise will be resolved within 180 days.
Original story: On November 22, 2022, Paul Moore, a security researcher and product tester, reported that, while reviewing a Eufy doorbell camera, he discovered it was uploading unencrypted screenshots to Eufy’s AWS cloud account. This data also included facial recognition thumbnail images, with identifiable information attached such as usernames.
He also noted that he could view the camera stream without authentication, later elaborating in a retweet that this can be accomplished with an app like VLC, though I saw no mention that you’d need to enable Real-Time Streaming Protocol (RTSP) on the camera. In my testing, I was able to replicate this on my network, but not when I took my phone off the network, as his tweet implied (it’s possible he was using a different method to get the streaming link than me, however).
The discovery of the uploaded images came from finding API calls made by the HomeBase, which revealed the location of the images, as well as the encryption key. Moore has been in regular contact with Eufy since his initial report, and tweeted on November 28 that Eufy has removed the background call and encrypted others so it’s no longer possible to detect, and states this is not the appropriate way to handle this, but doesn’t elaborate why.
Eufy’s privacy commitment page states “recorded footage will be kept private. Stored locally. With military-grade encryption. And transmitted to you, and only you.” Interpreting this pedantically, this statement doesn’t necessarily mean it doesn’t store screenshots, but there’s no explicit communication that it does so, and that should change.
Eufy, it seems, agrees. In a statement reported by Android Central and published in the Eufy community forums, the company acknowledged the oversight and said it intends to change communication in both its app and marketing materials to reflect the thumbnail notification feature’s behavior, though no timeline was given for the update.
The statement also says the company complies with General Data Protection Regulation – the EU collection of rules governing tech companies’ usage of customer data – and the images are sent to its servers if and only if users enable thumbnails to be sent with notifications from its cameras, which is not the default. It likewise said the practice meets the push notification standards of both Apple and Firebase Cloud Messaging.
What about a fix?
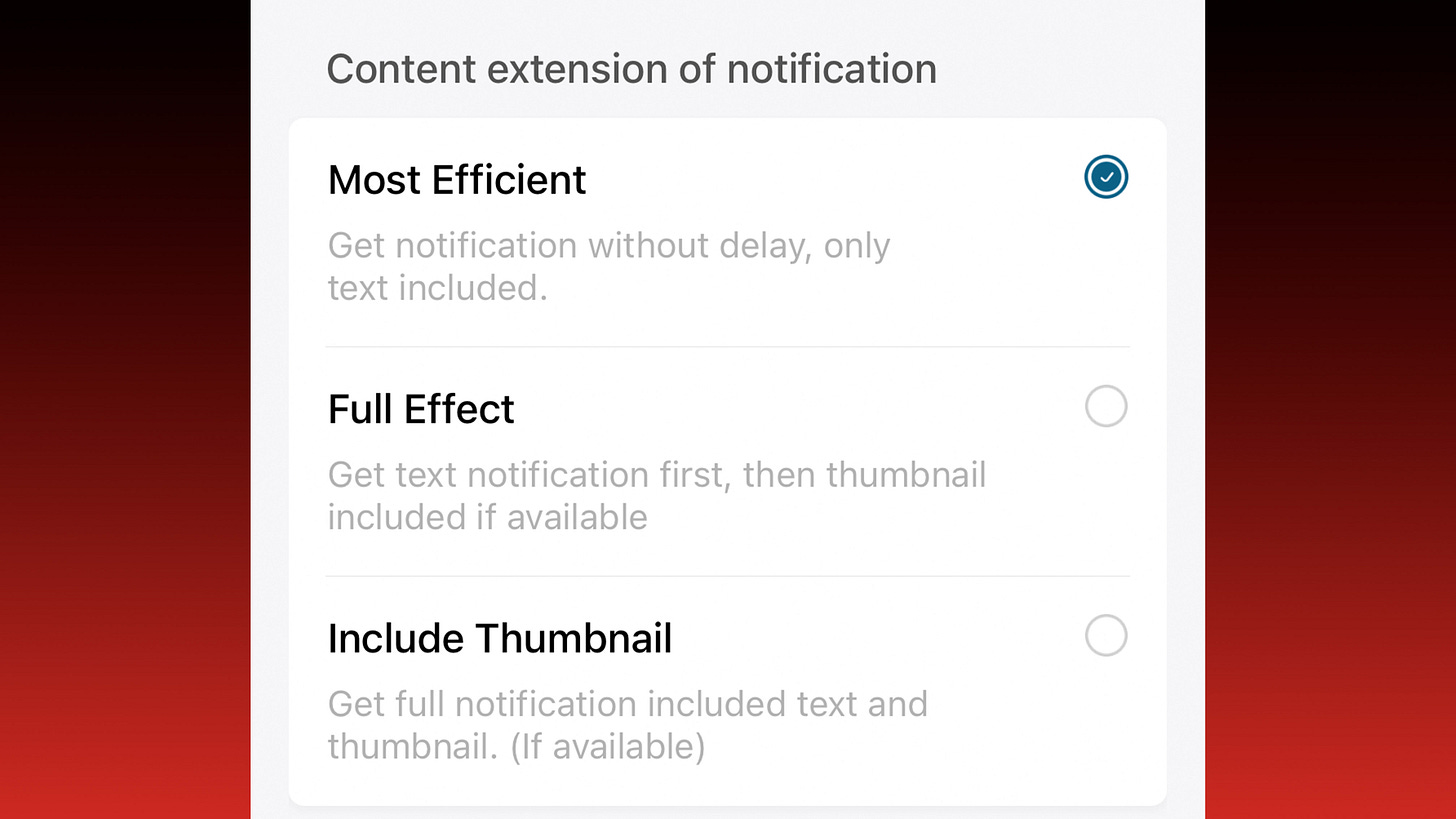
The Eufy Security iOS app was updated to version 4.5.0 within the last day as of this writing, but this update doesn’t appear to have changed the wording of the notification options screen for individual cameras:
Eufy is no stranger to privacy kerfuffles. In May 2021, an apparent software bug resulted in owners of the cameras being fed camera streams from other owners’ homes.
Eufy does seem to be moving quickly to address the issue, which appears to be limited to the screenshots Moore initially discovered. I’m concerned about the RTSP issue, but I’m not as familiar with the use of the protocol as I’d like to be and can’t make a judgment call here. I recently named the EufyCam 2C as the best camera for HomeKit users in my best home security cameras guide, and for now, I don’t believe that recommendation needs changing. Though I’ll be keeping my eye on the development of this story as I consider future updates to that page.
I’ve contacted Eufy to request clarification on when we should expect the changes to occur in both the app and marketing materials, and have requested a comment on RTSP authentication, and will update here when I know more.
In the meantime, if you have privacy concerns, it appears you need only make sure that RTSP is disabled and that individual camera notifications are set to Most Efficient, as the Full Effect and Include Thumbnail options both generate and upload video screenshots. If you’re unsure how to do each, simply reverse the instructions at the above links.
Updated: December 2, 2022